Most people have heard of the term phishing and have, at some point, been targeted by a phishing attempt in one form or another. But would you know what to do if a TOAD attacks? In this article we’ll take you through this new threat, explain what it is, the types of scam in operation and show you how to protect both you and your firm.
Although the phrase "TOAD attack" may sound bizarre, it's actually an easy-to-remember descriptor for a dangerous new threat plaguing businesses.
TOAD stands for Telephone-Oriented Attack Delivery, a form of multi-layered attack that combines elements of fraudulent contact, like text or instant message (smishing), voice call (vishing), QR Codes (QRishing) or email (phishing).
It includes social engineering techniques designed to trick users into compromising technology or disclosing company, personal, or financial data for the purpose of financial gain or malicious activity.
The rise of the TOAD
Before attacking, scammers will collect a victim's credentials and contact details from a variety of sources, such as previous data breaches, social media profiles and information purchased on the dark web. The victim then receives a message impersonating a reputable company or trusted authority with a fictional request which invokes a sense of urgency. The scammer uses the information they've gathered to 'prove' they are who they claim to be.
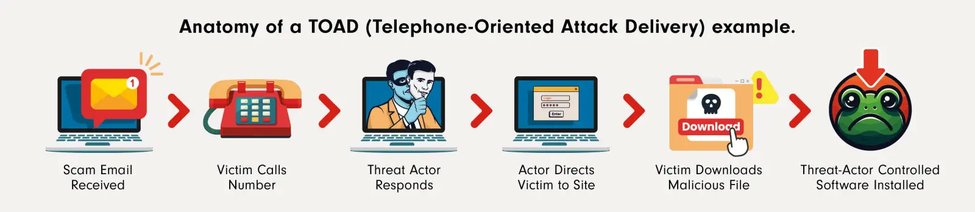
After trust is established, they're likely to call the victim to talk them through resolving the invented ‘situation’ or they may send a supplementary text or email. Either way, the goal is to encourage the victim to click on a malicious link which will install malware onto devices, download an attachment to enable them to bypass traditional cyber defences, such as MFA (Multi-Factor authentication) or trick the victim into completing actions which will compromise their data, money or identity.
Know your TOAD
According to the Proofpoint 2024 State of the Phish Report 10 million TOAD attack messages are sent every month and last year 67% of businesses globally were affected with this type of attack. To help you spot and stop one, here are three common examples showing how the attacks can work:
Invoice: Subscription Scam
Detail: You receive an email stating your account has been debited for auto renewal of a subscription. It goes on to state that you have 24 hours to call the company to cancel the payment.
Result: You are directed to a fake support site to download a file to ‘scan your system’ when it’s really trawling your computer, collecting personal info and passwords.
Shopping: Purchase Scam
Detail: You receive an email confirming a purchase you have supposedly made and requesting you contact the company immediately if you in fact did not place the order in question.
Result: You confirm your account/personal details and are then directed to download remote access software which provides the scammer with access to your computer.
Financial: Bank Scam
Detail: You are contacted via text message and informed that a bank account has been opened in your name. You are then requested to call the financial institute to confirm.
Result: You call scammer (or the scammer spoofs the real bank’s phone number and calls you) and are instructed to transfer money which is redirected to the fraudsters account.
Three simple steps to protect your and your firm from TOAD attacks
- Be cautious: Due to their multi-channel approach and targeting of specific individuals, we must all be on high alert for TOAD attacks. Check any emails/messages/calls you receive carefully for signs of phishing.
- Question everything: Before you act, ask yourself a few simple questions about the email/message/call:
a. Were you expecting it?
b. Do you know the person contacting you? Be aware; contact details like senders names, phone numbers and email addresses can be faked
c. What are you being asked to do? Is there a sense of urgency or an ‘act-now’ call to action - Investigate: Check and verify before you action any requests. Be cautious about calling phone numbers provided; always go to a reputable site and use the direct phone number listed or look the phone number up independently.
How we protect you and your clients
We understand the importance of keeping your firm’s and your clients’ information safe and secure. We use proven, industry-recognised security tools and processes to protect against fraud and security breaches and we regularly upgrade this protection in response to advances in security threats.
Fidelity is a member of Cifas, the UK’s fraud prevention agency, which works closely with law enforcement partners. Cifas Protective Registration is a fraud protection scheme that helps us protect your clients should they be at risk of fraud.
If you have any concerns about security, please call us as soon as possible on 0800 358 7717.
Latest articles
Pension freedoms and the road ahead
What key opportunities for advice firms may be going forward?
New retirement income approaches gaining in popularity
Drawdown has largely been acknowledged as the ‘winner’ in terms of product si…
Is there a missing asset class for retirees?
Conventional wisdom is that bonds and equities are negatively correlated. Whe…


